
PRODUCT

Smarter Biometrics, Stronger Digital Identity.
VIEW ALL
product finder
solution
case study
support
Company

Identifying the World. Easily, Securely.


years of solid experience
20+
.jpg)
400+
customised projects



EN
.avif)
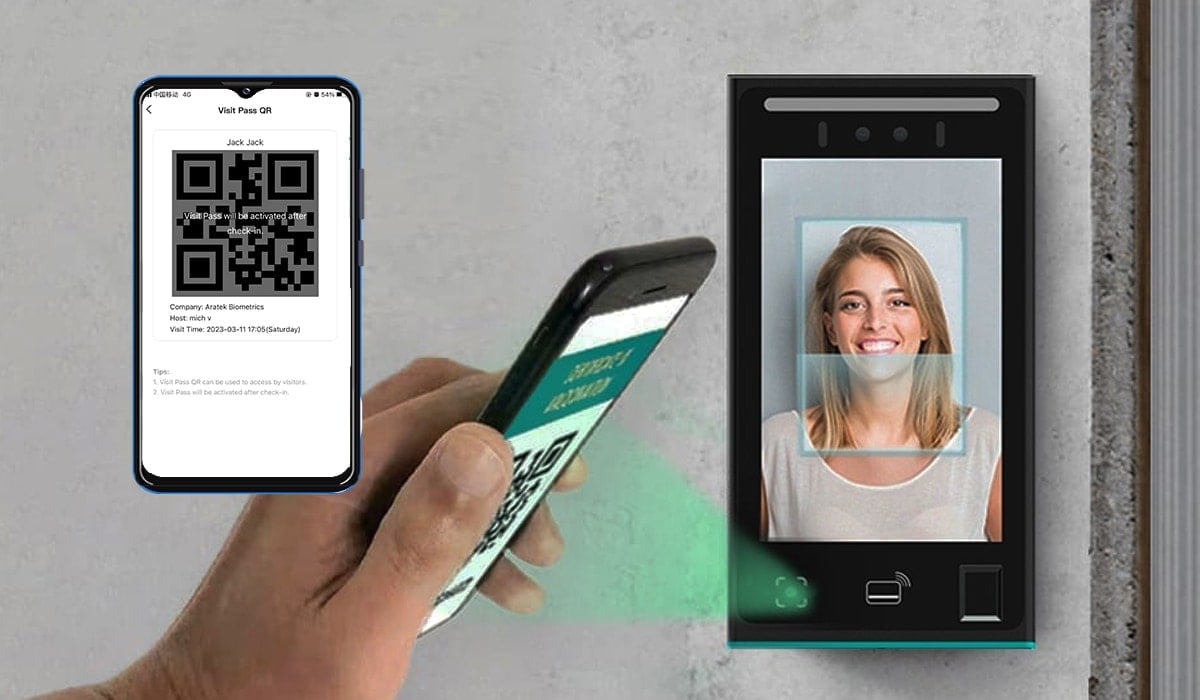
In today's fast-paced and security-conscious world, ensuring safe and efficient access to various spaces is more crucial than ever. QR code access control systems offer a sophisticated yet straightforward solution to manage entry into buildings, events, and restricted areas. But are these systems the right fit for your security needs? Let's explore the mechanics, benefits, and considerations of using QR codes for access control to help you make an informed decision.
A QR code access control system is a security mechanism that utilizes Quick Response codes to regulate and monitor access to physical and restricted areas. This system leverages the versatility and data storage capacity of QR codes to authenticate entry permissions efficiently.

At its core, a QR code access control system involves generating unique QR codes for users. These codes are typically tied to specific access permissions and can be customized for single use, multiple uses, or a limited time period.
A QR code access control system is composed of several key elements that ensure its effective operation:
{{product-cta}}
The QR code access control system harnesses the simplicity and familiarity of QR code technology to provide flexible and user-friendly access management solutions. By incorporating QR codes, these systems offer a versatile and easily understandable approach to controlling access, making them an effective component of modern security strategies.
A QR code access control system operates through a series of steps designed to authorize entry based on QR codes. This section breaks down the process to provide a clear understanding of how these systems function in real-world scenarios.
The process begins with the generation of unique QR codes for each user. These codes are created based on specific access permissions and user credentials, which can be customized for various use cases:
The QR code generator software plays a critical role in creating these unique codes, embedding the necessary data securely.
Once generated, QR codes are distributed to users via electronic means, ensuring a seamless and contactless delivery method:
This distribution method eliminates the need for physical cards or keys, enhancing convenience and reducing administrative overhead.
At the entry point, users present their QR codes to a QR code reader, which scans and decodes the information:
The decoded data is then transmitted to the access control server for verification against stored credentials:
Based on the verification results, the system either grants or denies access:
Once a visitor's access period ends, the system ensures that their QR code is no longer valid:
All access events are logged and monitored through the system administration software:
Through these steps, QR code access control systems provide a structured approach to managing building access control systems. By leveraging QR code readers and mobile devices, these systems enable efficient and secure entry management. Users can receive their QR codes on their mobile phones, facilitating easy access and streamlined operations.
To ensure the security and integrity of QR code access control systems, implementing a variety of security measures is essential. These measures help mitigate risks such as code duplication, unauthorized sharing, and other potential breaches. Below are several strategies to consider:
Adding an extra layer of security by requiring a second form of identification can significantly reduce unauthorized physical access risks. This can include:
Limiting the validity of QR codes can prevent unauthorized access from copied or shared codes:
Ensuring the security of QR codes and data transmission is crucial to prevent interception and unauthorized decoding:
Implementing systems to monitor access in real-time and alert security personnel to any unusual activity is vital:
Incorporating advanced QR code technologies can enhance security:
Continuously reviewing and updating access control policies and technologies is important:
Educating users on the proper use and risks associated with QR code access can reduce the likelihood of security breaches:
Implementing these comprehensive security measures can significantly enhance the effectiveness and reliability of QR code access control systems, ensuring they are secure against a wide array of potential threats.
QR code access control systems can be integrated with various other physical security and operational systems, enhancing overall functionality and user experience:
By integrating with visitor management systems, QR codes streamline the check-in process, improving both security and visitor tracking. This integration allows pre-registered visitors to receive QR codes via SMS or email that grant access for a limited time period, tailored to the duration of their visit. It significantly enhances the visitor experience by making the check-in process faster and more convenient.
QR codes can also be used in conjunction with time and attendance systems, particularly in field operations or remote work environments. Employees can scan their QR codes at various locations to log their working hours accurately, providing a reliable way to track attendance without the need for physical time clocks.
In the context of events, QR codes serve dual functions—facilitating secure access control and attendee management. They can quickly verify entry permissions and simultaneously track attendance, which is particularly useful for events with multiple entry points and sessions.
These integrations illustrate the flexibility and utility of QR code access control systems, making them a valuable component in a comprehensive security strategy.
For organizations evaluating their security needs and considering QR code access control systems, understanding their suitability and benefits is crucial. This section addresses key considerations for those unsure if QR code access control is the right solution for their facility.
Before implementing a QR code access control system, it’s essential to evaluate your specific security requirements:
When deciding to implement a QR code access control system, consider the following practical aspects:
Implementing a QR code access control system can offer several advantages over conventional bar codes:
Determining whether a QR code access control system is right for your facility involves assessing your security needs, understanding the advantages, and considering how it can enhance your existing security measures. QR code systems offer a robust and efficient security framework that ensures secure and convenient access management. For more detailed insights and customized solutions, consult with our experts to find the best fit for your organization's unique requirements.
Determining whether a QR code access control system is right for your facility involves a thorough assessment of your security needs, understanding the unique advantages these systems offer, and considering their integration with existing security measures.
QR code access control systems provide several key benefits: they offer high efficiency and cost-effectiveness. By enabling quick access through mobile devices, administrators can manage entry and exit seamlessly, ensuring better control of people flow and reducing congestion at access points. Additionally, these systems significantly lower the need for physical key fobs or plastic ID cards, simplifying access management and reducing overall costs.
However, it is important to be aware of potential security challenges, such as the possibility of code sharing and the risk of QR codes being copied or duplicated. Implementing comprehensive security measures, including multi-factor authentication, time-based restrictions, and real-time monitoring, can help mitigate these risks. Regular audits and user education are also essential to maintaining the system’s integrity.
While QR code access control systems offer numerous advantages, it's crucial to weigh these benefits against the potential drawbacks and tailor the system to meet your specific needs. By carefully considering these factors, your organization can implement a QR code access control system that enhances security, improves operational efficiency, and provides a flexible solution for managing access to your facilities.
.avif)
Use our product finder to pinpoint the ideal product for your needs.


















